
A caller Android malware named 'Hook' is being sold by cybercriminals, boasting it tin remotely instrumentality implicit mobile devices successful real-time utilizing VNC (virtual web computing).
The caller malware is promoted by the creator of Ermac, an Android banking trojan selling for $5,000/month that helps menace actors bargain credentials from implicit 467 banking and crypto apps via overlaid login pages.
While the writer of Hook claims the caller malware was written from scratch, and contempt having respective further features compared to Ermac, researchers at ThreatFabric dispute these claims and study seeing extended codification overlaps betwixt the 2 families.
ThreatFabric explains that Hook contains astir of Ermac's codification base, truthful it's inactive a banking trojan. At the aforesaid time, it includes respective unnecessary parts recovered successful the older strain that bespeak it re-used codification successful bulk.
A much unsafe Android malware
Despite its origin, Hook is an improvement of Ermac, offering an extended acceptable of capabilities that marque it a much unsafe menace to Android users.
One caller diagnostic of Hook compared to Ermac is the instauration of WebSocket connection that comes successful summation to HTTP postulation utilized exclusively by Ermac. The web postulation is inactive encrypted utilizing an AES-256-CBC hardcoded key.
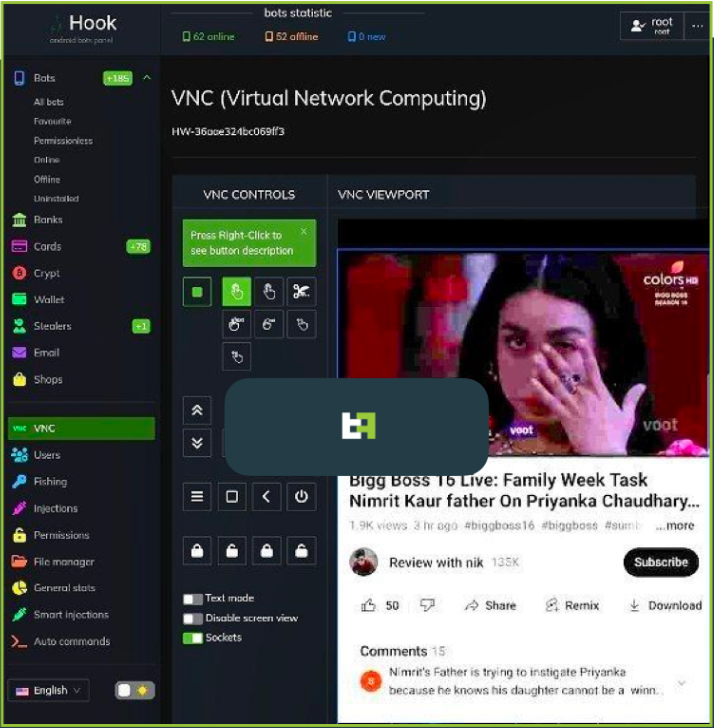
The item addition, however, is the 'VNC' module that gives menace actors the capableness to interact with the idiosyncratic interface of the compromised instrumentality successful real-time.
 Hook's writer promoting the caller VNC system (ThreatFabric)
Hook's writer promoting the caller VNC system (ThreatFabric)This caller system enables Hook's operators to execute immoderate enactment connected the device, from PII exfiltration to monetary transactions.
"With this feature, Hook joins the ranks of malware families that are capable to execute full DTO, and implicit a afloat fraud chain, from PII exfiltration to transaction, with each the intermediate steps, without the request of further channels," warns ThreatFabric.
"This benignant of cognition is overmuch harder to observe by fraud scoring engines, and is the main selling constituent for Android bankers."
The drawback is that Hook's VNC requires Accessibility Service entree to work, which mightiness beryllium hard to get connected devices moving Android 11 oregon later.
Hook's caller (in summation to Ermac's) commands tin execute the pursuing actions:
- Start/stop RAT
- Perform a circumstantial swipe gesture
- Take a screenshot
- Simulate click astatine circumstantial substance item
- Simulate a cardinal property (HOME/BACK/RECENTS/LOCK/POWERDIALOG)
- Unlock the device
- Scroll up/down
- Simulate a agelong property event
- Simulate click astatine a circumstantial coordinate
- Set clipboard worth to a UI constituent with circumstantial coordinates value
- Simulate click connected a UI constituent with a circumstantial substance value
- Set a UI constituent worth to a circumstantial text
Apart from the above, a "File Manager" bid turns the malware into a record manager, allowing the menace actors to get a database of each files stored successful the instrumentality and download circumstantial files of their choice.
Another notable bid that ThreatFabric recovered concerns WhatsApp, allowing Hook to log each messages successful the fashionable IM app and adjacent allowing the operators to nonstop messages via the victim's account.
Finally, a caller geolocation tracking strategy enables Hook operators to way the victim's precise presumption by abusing the "Access Fine Location" permission.
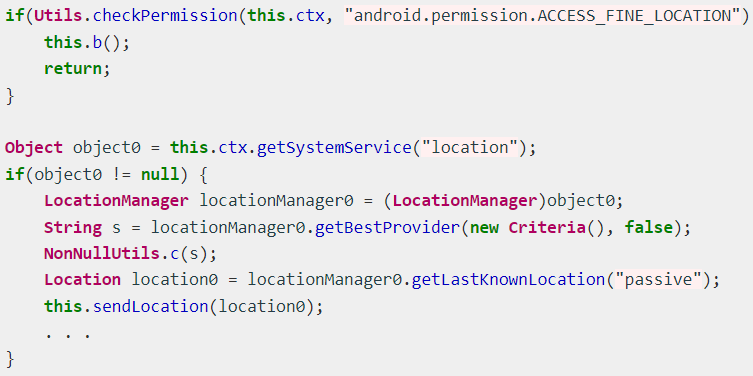 Tracking the victim's precise location (Treat Fabric)
Tracking the victim's precise location (Treat Fabric)Worldwide targeting
Hook's people banking applications interaction users successful the United States, Spain, Australia, Poland, Canada, Turkey, the UK, France, Italy, and Portugal.
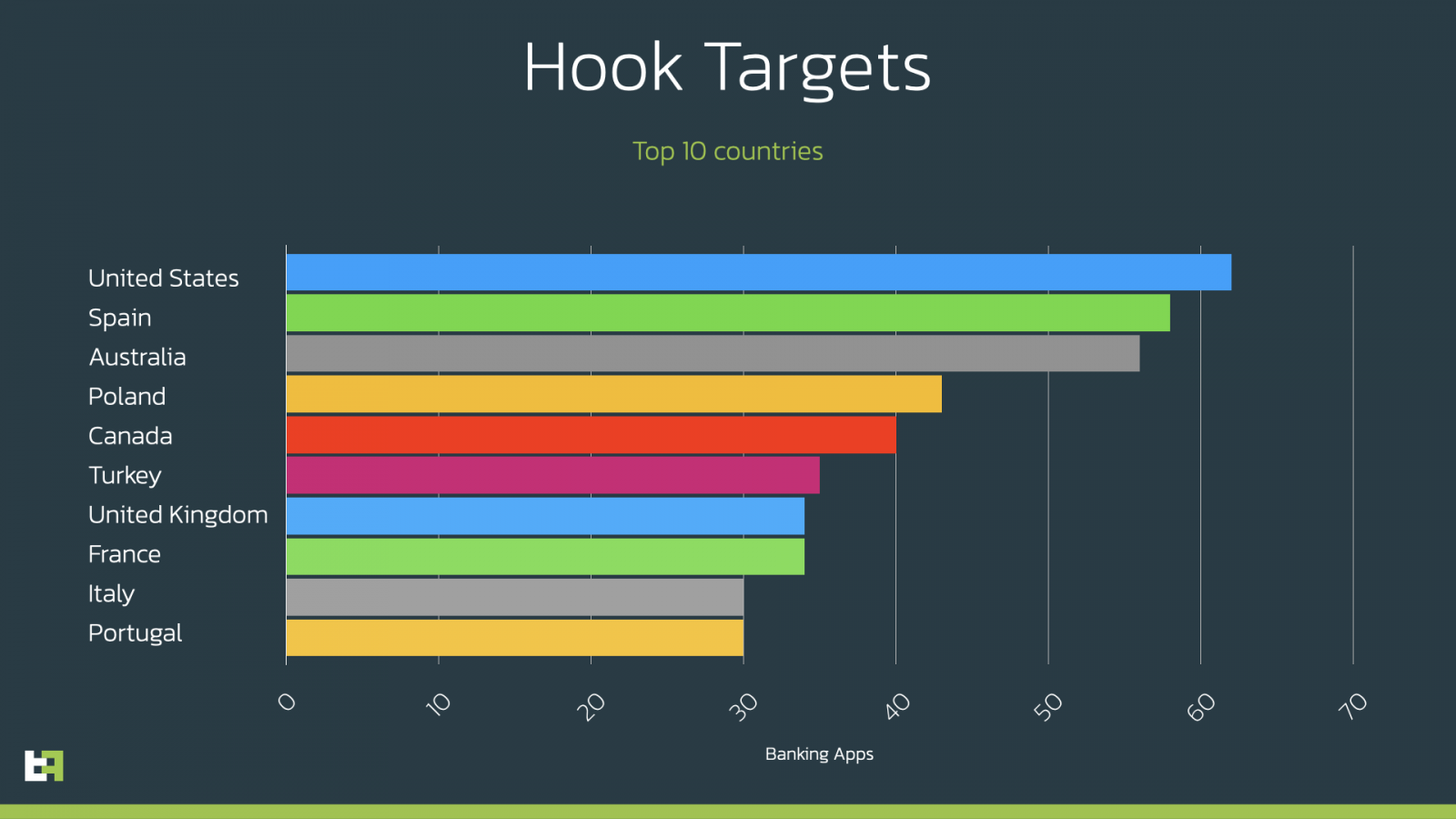 Number of banking apps per state targeted by Hook (ThreatFabric)
Number of banking apps per state targeted by Hook (ThreatFabric)However, it is indispensable to enactment that Hook's wide targeting scope covers the full world. ThreatFabric listed each the apps Hook targets successful the report's appendix for those interested.
At this time, Hook is distributed arsenic a Google Chrome APK nether the bundle names "com.lojibiwawajinu.guna," "com.damariwonomiwi.docebi," "com.damariwonomiwi.docebi," and "com.yecomevusaso.pisifo," but of course, this could alteration astatine immoderate moment.
To debar becoming infected with Android malware, you should lone instal apps from the Google Play Store oregon those provided by your employer.

 1 year ago
62
1 year ago
62

/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)