
A information probe steadfast says it discovered an “easily” exploitable vulnerability successful a doorway introduction information strategy utilized successful authorities buildings and flat complexes, but warns that the vulnerability cannot beryllium fixed.
Norwegian information institution Promon says the bug affects respective Aiphone GT models that usage NFC technology, often recovered successful contactless recognition cards, and allows atrocious actors to perchance summation entree to delicate facilities by brute-forcing the doorway introduction system’s information code.
Door introduction systems let secure entree to buildings and residential complexes, but person go progressively digitized, making them susceptible to some carnal and distant compromise.
Aiphone counts some the White House and the U.K. Parliament arsenic customers of the affected systems, according to institution brochures seen by TechCrunch.
Promon information researcher Cameron Lowell Palmer said a would-be intruder tin usage an NFC-capable mobile instrumentality to rapidly rhythm done each permutation of a four-digit “admin” codification utilized to unafraid each Aiphone GT doorway system. Because the strategy does not bounds however galore times a codification tin beryllium tried, Palmer said it takes lone minutes to rhythm done each of the 10,000 imaginable four-digit codes utilized by the doorway introduction system. That codification tin beryllium punched into the system’s keypad, oregon transmitted to an NFC tag, allowing atrocious actors to perchance entree restricted areas without having to interaction the strategy astatine all.
In a video shared with TechCrunch, Palmer built a proof-of conception Android app that allowed him to cheque each four-digit codification connected a susceptible Aiphone doorway introduction strategy successful his trial lab. Palmer said the affected Aiphone models bash not store logs, allowing a atrocious histrion to bypass the system’s information without leaving a integer trace.
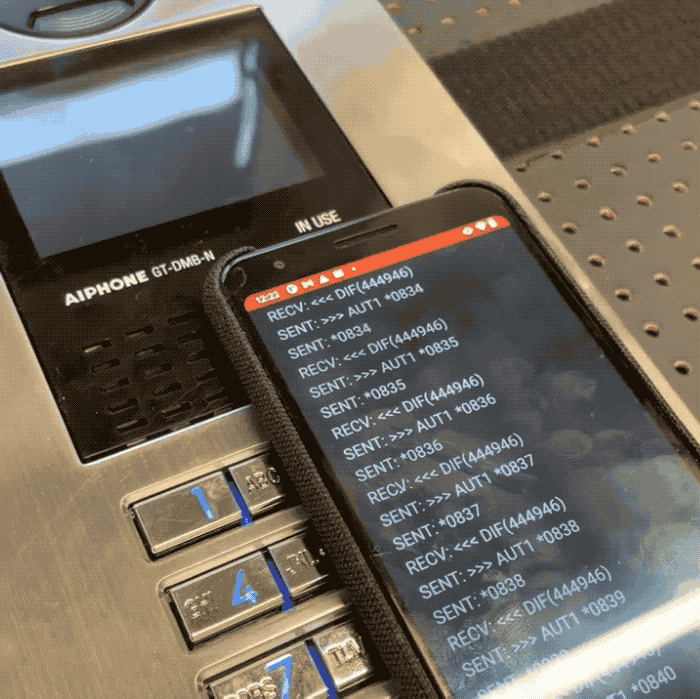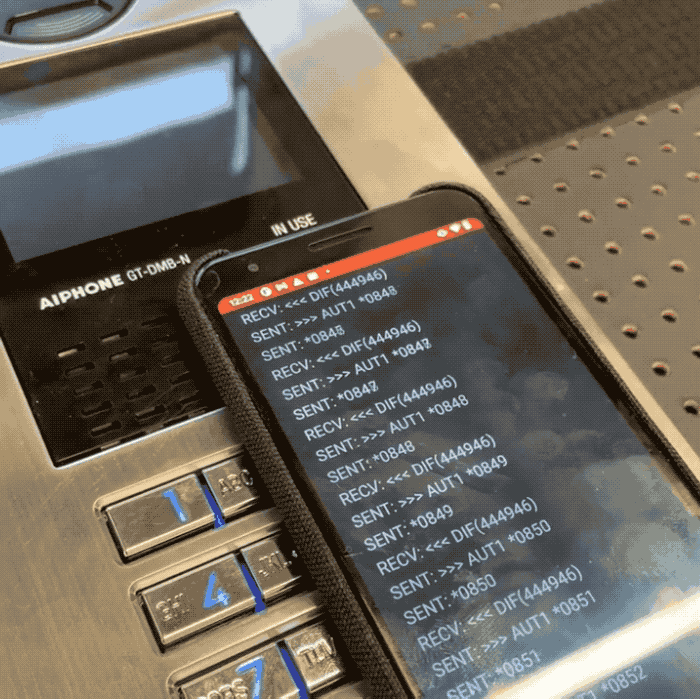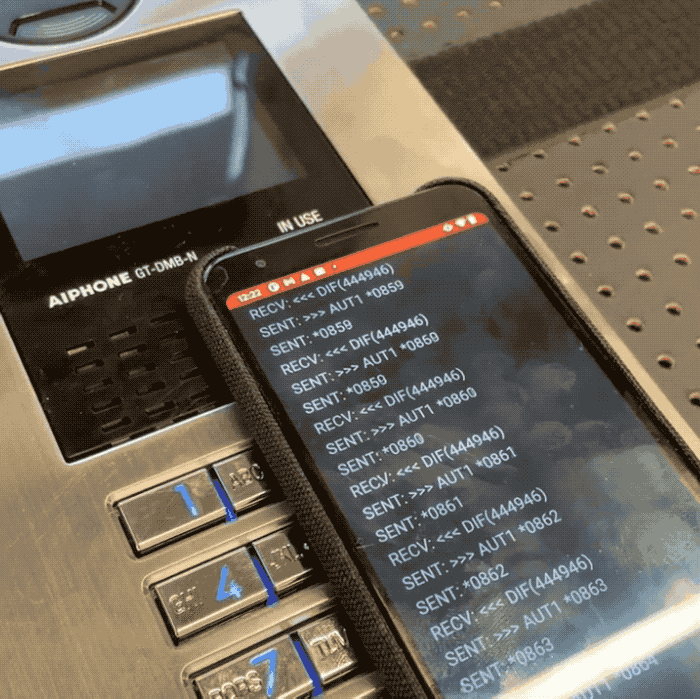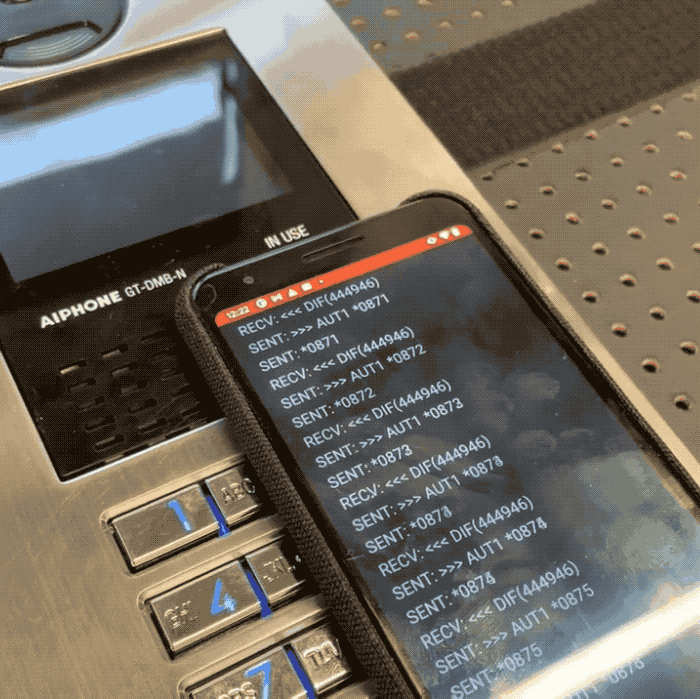
Image Credits: Cameron Lowell Palmer / Promon
Palmer disclosed the vulnerability to Aiphone successful precocious June 2021. Aiphone told the information institution that systems manufactured earlier December 7, 2021 are affected and cannot beryllium updated, but that systems aft this day person a bundle hole that limits the complaint of doorway introduction attempts.
It’s not the lone bug that Promon discovered successful the Aiphone system. Promon besides said it discovered that the app utilized to acceptable up the doorway introduction strategy offers an unencrypted, plaintext record that contains the head codification for the system’s back-end portal. Promon said that could let an intruder to besides entree the accusation needed to entree restricted areas.
Aiphone spokesperson Brad Kemcheff did not respond to requests for remark sent anterior to publication.
Relatedly, a assemblage pupil and information researcher earlier this twelvemonth discovered a “master key” vulnerability successful a widely utilized doorway introduction system built by CBORD, a tech institution that provides entree power and outgo systems to hospitals and assemblage campuses. CBORD fixed the bug aft the researcher reported the contented to the company.

 2 years ago
42
2 years ago
42

/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)