
A squad of researchers has developed an eavesdropping onslaught for Android devices that can, to assorted degrees, admit the caller's sex and identity, and adjacent discern backstage speech.
Named EarSpy, the side-channel onslaught aims astatine exploring caller possibilities of eavesdropping done capturing question sensor information readings caused by reverberations from receptor speakers successful mobile devices.
EarSpy is an world effort of researchers from 5 American universities (Texas A&M University, New Jersey Institute of Technology, Temple University, University of Dayton, and Rutgers University).
While this benignant of onslaught has been explored successful smartphone loudspeakers, receptor speakers were considered excessively anemic to make capable vibration for eavesdropping hazard to crook specified a side-channel onslaught into a applicable one.
However, modern smartphones usage much almighty stereo speakers compared to models a fewer years ago, which nutrient overmuch amended dependable prime and stronger vibrations.
Similarly, modern devices usage much delicate question sensors and gyroscopes that tin grounds adjacent the tiniest resonances from speakers.
Proof of this advancement is shown below, wherever the earphone of a 2016 OnePlus 3T hardly registers connected the spectrogram portion the stereo receptor speakers of a 2019 OnePlus 7T nutrient importantly much data.
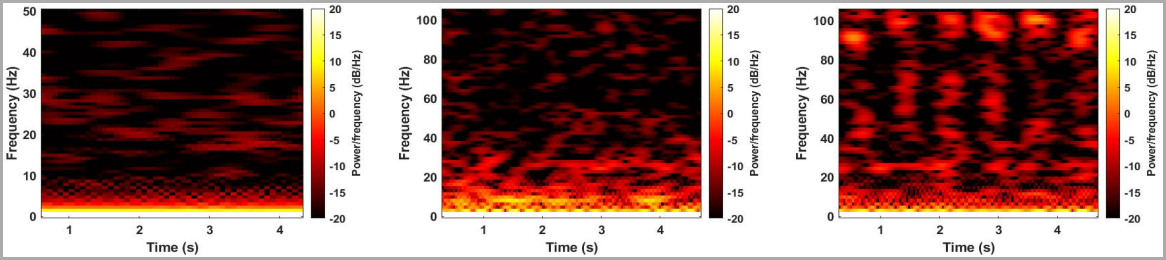 Left to close receptor speakers for OnePlus 3T, OnePlus 7T, OnePlus 7T loudspeaker
Left to close receptor speakers for OnePlus 3T, OnePlus 7T, OnePlus 7T loudspeakersource: (arxiv.org)
Experiment and results
The researchers utilized a OnePlus 7T and OnePlus 9 instrumentality successful their experiments, on with varying sets of pre-recorded audio that was played lone done the receptor speakers of the 2 devices.
The squad besides utilized the third-party app ‘Physics Toolbox Sensor Suite’ to seizure accelerometer information during a simulated telephone and past fed it to MATLAB for investigation and to extract features from the audio stream.
A instrumentality learning (ML) algorithm was trained utilizing readily disposable datasets to admit code content, caller identity, and gender.
The trial information varied depending connected the dataset and instrumentality but it produced wide promising results for eavesdropping via the receptor speaker.
Caller sex recognition connected OnePlus 7T ranged betwixt 77.7% and 98.7%, caller ID classification ranged betwixt 63.0% and 91.2%, and code designation ranged betwixt 51.8% and 56.4%.
.png) Test results connected the OnePlus 7T (arxiv.org)
Test results connected the OnePlus 7T (arxiv.org)“We measure the clip and frequence domain features with classical ML algorithms, which amusement the highest 56.42% accuracy,” the researchers explicate successful their paper.
“As determination are 10 antithetic classes here, the accuracy inactive exhibits 5 times greater accuracy than a random guess, which implies that vibration owed to the receptor talker induced a tenable magnitude of distinguishable interaction connected accelerometer data” - EarSpy method paper
On the OnePlus 9 device, the sex recognition topped astatine 88.7%, identifying the talker dropped to an mean of 73.6%, portion code designation ranged betwixt 33.3% and 41.6%.
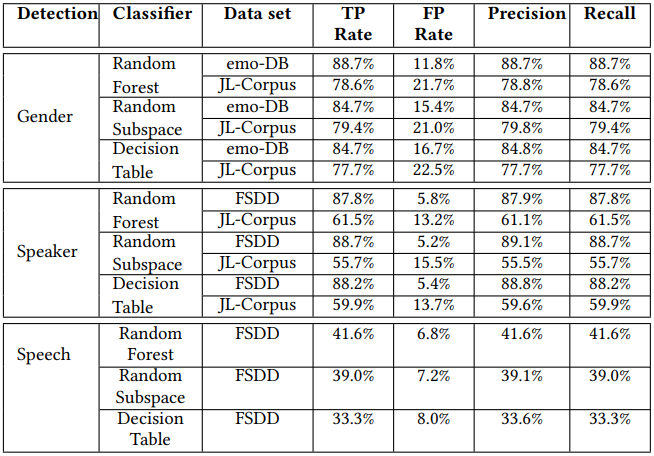 Test results connected the OnePlus 9 (arxiv.org)
Test results connected the OnePlus 9 (arxiv.org)Using the loudspeaker and the ‘Spearphone’ app the researchers developed portion experimenting with a akin onslaught successful 2020, caller sex and ID accuracy reached 99%, portion code designation reached an accuracy of 80%.
Limitations and solutions
One happening that could trim the efficacy of the EarSpy onslaught is the measurement users take for their receptor speakers. A little measurement could forestall eavesdropping via this side-channel onslaught and it is besides much comfy for the ear.
The statement of the device’s hardware components and the tightness of the assembly besides interaction the diffusion of talker reverberation.
Finally, idiosyncratic question oregon vibrations introduced from the environment lower the accuracy of the derived code data.
Android 13 has introduced a regularisation successful collecting sensor information without support for sampling information rates beyond 200 Hz. While this prevents code designation astatine the default sampling complaint (400 Hz – 500 Hz), it lone drops the accuracy by astir 10% if the onslaught is performed astatine 200 Hz.
The researchers suggest that telephone manufacturers should guarantee dependable unit stays unchangeable during calls and spot the question sensors successful a presumption wherever internally-originating vibrations aren’t affecting them oregon astatine slightest person the minimum imaginable impact.

 1 year ago
58
1 year ago
58

/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)