
Google's Threat Analysis Group (TAG) revealed contiguous that a radical of North Korean hackers tracked arsenic APT37 exploited a antecedently chartless Internet Explorer vulnerability (known arsenic a zero-day) to infect South Korean targets with malware.
Google TAG was made alert of this caller onslaught connected October 31 erstwhile aggregate VirusTotal submitters from South Korea uploaded a malicious Microsoft Office papers named "221031 Seoul Yongsan Itaewon mishap effect concern (06:00).docx."
Once opened connected the victims' devices, the papers would present an chartless payload aft downloading a affluent substance record (RTF) distant template that would render distant HTML utilizing Internet Explorer.
Loading the HTML contented that delivered the exploit remotely allows the attackers to exploit the IE zero-day adjacent if the targets weren't utilizing it arsenic their default web browser.
The vulnerability (tracked as CVE-2022-41128) is owed to a weakness successful the JavaScript motor of Internet Explorer, which allows menace actors who successfully exploit it to execute arbitrary codification erstwhile rendering a maliciously crafted website.
Microsoft patched it during last month's Patch Tuesday, connected November 8, 5 days aft assigning it a CVE ID pursuing a study from TAG received connected October 31.
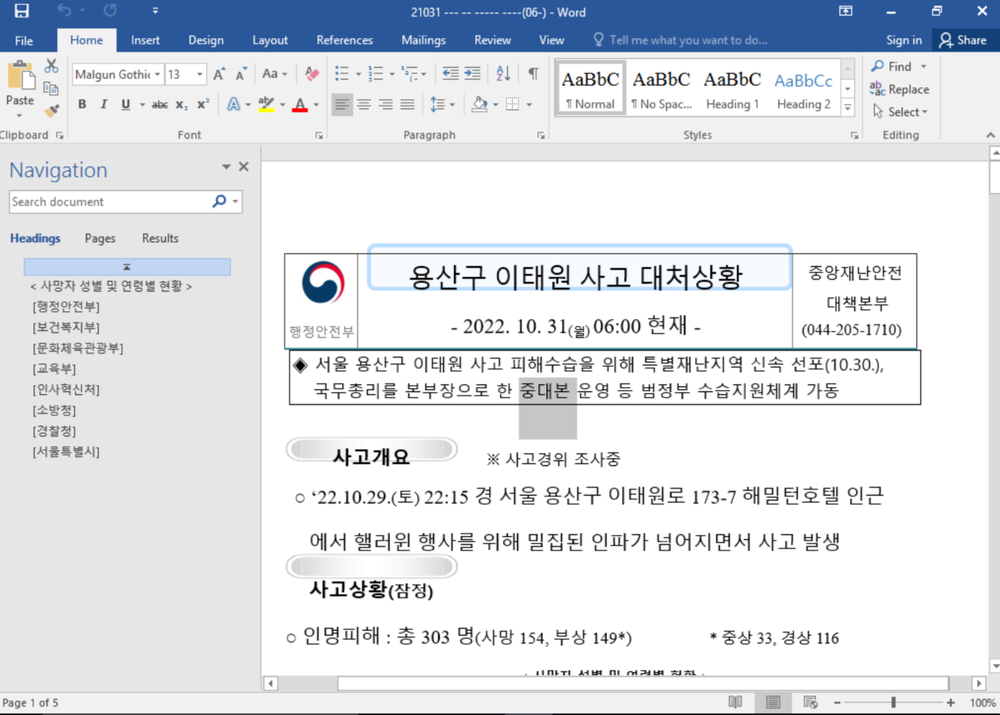 Malicious Office papers utilized arsenic lure by APT37 hackers (Google TAG)
Malicious Office papers utilized arsenic lure by APT37 hackers (Google TAG)No accusation connected malware pushed to victims' devices
While Google TAG couldn't analyse the last malicious payload distributed by the North Korean hackers connected their South Korean targets' computers, the menace actors are known for deploying a wide scope of malware successful their attacks.
"Although we did not retrieve a last payload for this campaign, we've antecedently observed the aforesaid radical present a assortment of implants similar ROKRAT, BLUELIGHT, and DOLPHIN," Google TAG's Clement Lecigne and Benoit Stevens said.
"APT37 implants typically maltreatment morganatic unreality services arsenic a C2 transmission and connection capabilities emblematic of astir backdoors."
APT37 has been progressive for astir a decade, since astatine slightest 2012, and was previously linked to the North Korean government with precocious assurance by FireEye.
The menace radical is known for focusing its attacks connected individuals of involvement to the North Korean regime, including dissidents, diplomats, journalists, quality rights activists, and authorities employees.


/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)