An Internet Explorer zero-day vulnerability was actively exploited by a North Korean menace histrion to people South Korean users by capitalizing connected the caller Itaewon Halloween assemblage crush to instrumentality users into downloading malware.
The discovery, reported by Google Threat Analysis Group researchers Benoît Sevens and Clément Lecigne, is the latest acceptable of attacks perpetrated by ScarCruft, which is besides called APT37, InkySquid, Reaper, and Ricochet Chollima.
"The radical has historically focused their targeting connected South Korean users, North Korean defectors, argumentation makers, journalists, and quality rights activists," TAG said successful a Thursday analysis.
The caller findings exemplify the menace actor's continued maltreatment of Internet Explorer flaws specified arsenic CVE-2020-1380 and CVE-2021-26411 to driblet backdoors similar BLUELIGHT and Dolphin, the second of which was disclosed by Slovak cybersecurity steadfast ESET precocious past month.
Another cardinal instrumentality successful its arsenal is RokRat, a Windows-based distant entree trojan that comes with a wide scope of functions that let it to seizure screenshots, log keystrokes, and adjacent harvest Bluetooth instrumentality information.
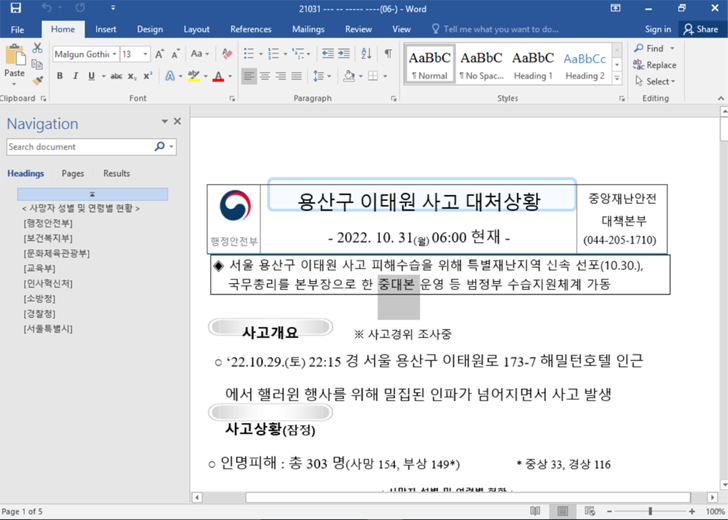
The onslaught concatenation observed by Google TAG entails the usage of a malicious Microsoft Word papers that was uploaded to VirusTotal connected October 31, 2022. It abuses yet different Internet Explorer zero-day flaw successful the JScript9 JavaScript engine, CVE-2022-41128, that was patched by Microsoft past month.
The record references the October 29 incidental that took spot successful the Itaewon vicinity of Seoul and exploits nationalist involvement successful the calamity to retrieve an exploit for the vulnerability upon opening it. The onslaught is enabled by the information that Office renders HTML contented utilizing Internet Explorer.
Successful exploitation is followed by the transportation of a shellcode that wipes each traces by clearing the Internet Explorer cache and past arsenic good arsenic downloading the adjacent signifier payload.
Google TAG said it could not retrieve the follow-on malware utilized successful the campaign, though it's suspected to person progressive the deployment of RokRat, BLUELIGHT, oregon Dolphin.
Found this nonfiction interesting? Follow america connected Twitter and LinkedIn to work much exclusive contented we post.




/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)