Apple products are regarded arsenic immoderate of the astir unafraid devices presently connected the market. Designed with an array of information programs, tools and features, you whitethorn beryllium wondering, bash iPhones request antivirus software, too?
Apple’s operating strategy (iOS) provides iPhones and different Apple devices with information features that marque it highly hard for malware to infiltrate. However, if the telephone has been tampered with, it whitethorn beryllium worthy taking further information measures to support your devices, specified arsenic installing antivirus software.
Can iPhones Get Viruses?
Like immoderate computer, an iPhone tin drawback a virus. Viruses enactment by infiltrating systems, attaching to programs, replicating themselves and attaching those copies to further programs. This allows them to communicate, bargain information and origin damage.
iOS is simply a closed ecosystem that restricts connection betwixt programs and requires each applications to beryllium approved by the App Store. These restrictions marque it hard for viruses to pass and spread. If the archetypal operating strategy is tampered with, however, similar if the iPhone is jailbroken oregon doesn’t person the latest update, the telephone becomes susceptible to microorganism attacks.
What Viruses and Other Threats Affect iPhones?
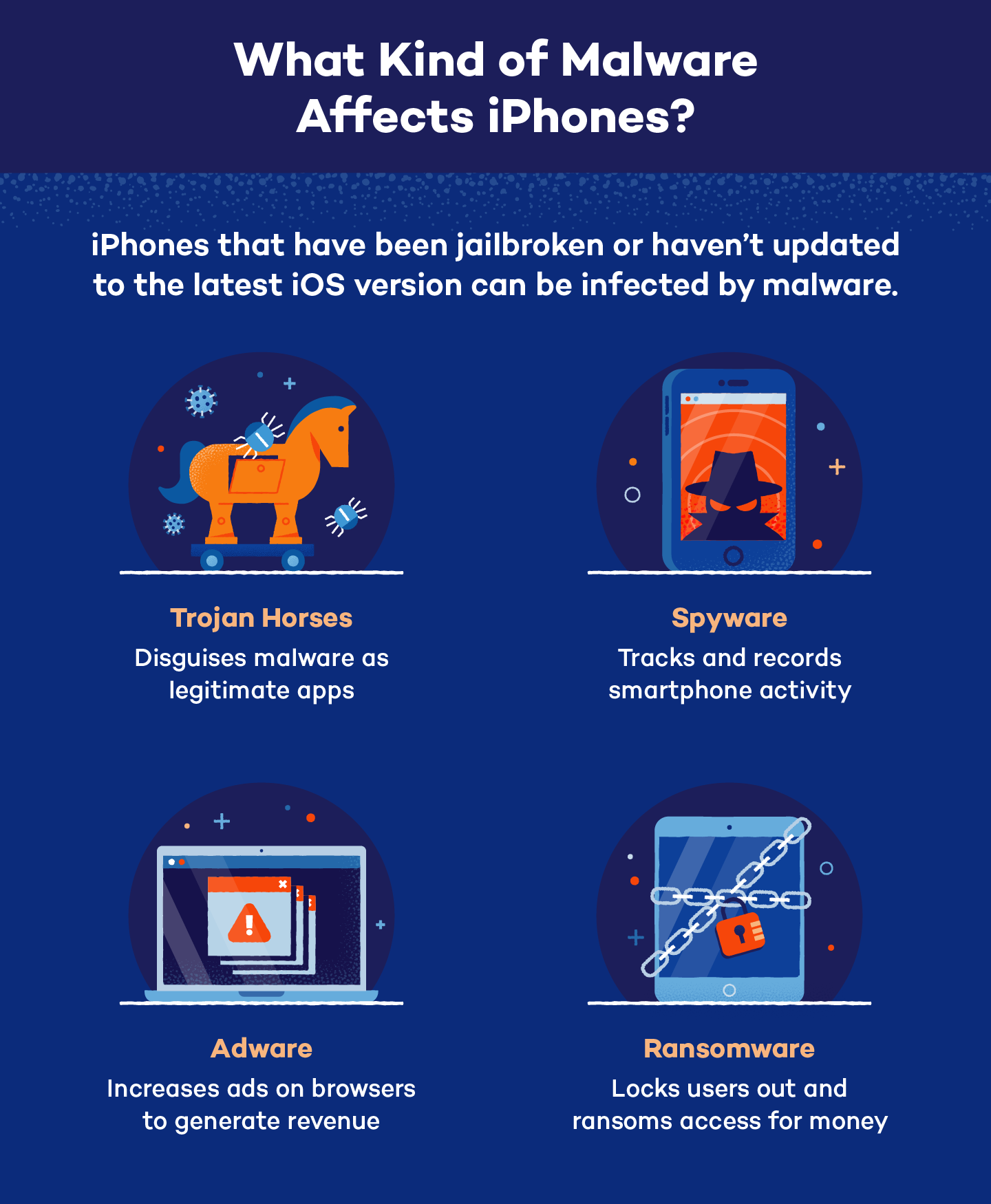
A microorganism is conscionable 1 benignant of malware that tin beryllium recovered connected an iPhone. There are galore types of iPhone viruses and different cyber threats that could impact your instrumentality if it has weakened security, including:
- Ransomware: a malware programme designed to lock users retired of their device successful bid to clasp entree to it astatine ransom for a sum of money
- Phishing: the enactment of sending fraudulent messages with suspicious links successful ads, messages, calls, voicemails, emails, oregon websites to users with the intent of stealing their individuality oregon different idiosyncratic information
- Data breaches: the amerciable entree of a instrumentality with the intent of stealing backstage oregon delicate information
- Spyware: a malware programme that records a user’s actions, specified arsenic calls, texts, locations, images, video, keystrokes and browsing history, to get delicate information
- Adware: a programme that causes incessant pop-up ads portion utilizing a browser, generating gross for developers each clip a idiosyncratic interacts with it
- Trojan horses: programs that are disguised arsenic guiltless apps that deploy malware onto devices erstwhile downloaded
Although these antithetic attacks person akin characteristics, specified arsenic the accusation they’re seeking oregon the channels they usage to infiltrate your device, it tin instrumentality a stockpile of protective features to combat them each astatine once.
How to Detect Viruses connected iPhones
One of the astir hard microorganism characteristics to woody with is its quality to stay unseen and undetectable. Many users whitethorn not adjacent beryllium alert that determination is simply a microorganism connected their iPhone.
However, determination are respective reddish flags that tin bespeak an iPhone has a virus, including:
- Overheating: Malware tin origin undetectable apps, widgets oregon programs to continuously tally successful the background, causing the processor to tally heavily, overheat and perchance unopen down.
- Excessive information usage: Similar to overheating, malware moving programs successful the inheritance whitethorn besides usage information to enactment connected to extracurricular networks.
- Pop-ups: If pop-up ads look portion you are browsing connected Safari informing of a microorganism infection, it’s not an authoritative Apple notification — Apple does not usage pop-ups for strategy warnings, and interacting with the advertisement tin pb to further contamination.
- Unknown oregon suspicious apps: Apps that look connected iPhones that you haven’t downloaded oregon that didn’t travel preinstalled whitethorn person been downloaded by a cybercriminals.
- Drained artillery life: Like overheating and information use, malware that causes inheritance programs to tally tin usage up powerfulness and drain batteries.
Of course, these signs bash not ever mean that an iPhone is infected. They whitethorn alternatively bespeak that the telephone is simply outdated, breached oregon old. However, due to the fact that an iPhone microorganism scan instrumentality is not preinstalled, the basal of these issues tin beryllium hard to determine. The astir effectual mode to instrumentality attraction of your instrumentality is to beryllium proactive with information measures.
Do iPhones Have Built-in Security?
Apple’s estimation of being the astir unafraid marque of smartphones and computers is successful portion owed to its multitude of built-in information features and programs for its devices. However, if thing happens to impair these features, specified arsenic missing an update, damaging the telephone oregon accidentally turning a diagnostic off, the iPhone would erstwhile again stay exposed to viruses and different threats.
Here’s a database of preinstalled Apple tools and features to support successful caput portion reasoning astir your phone’s security.
Fraudulent Website Warning
Fraudulent Website Warning is simply a Safari setting that indicates if the website you’re trying to sojourn is suspected of phishing. If Safari calculates that the tract is imitating a morganatic concern successful an effort to bargain your idiosyncratic data, it volition pass you and forestall entree to the site.
Two-factor Authentication for Apple ID
The Apple ID two-factor authentication diagnostic was released successful 2015 and is present a staple crossed astir each Apple ID account. Only usable with an further device, users are required to log successful by archetypal entering their password, and past inputting a six-figure codification that’s automatically sent to a trusted oregon antecedently authenticated 2nd device.
iCloud Private Relay
Similar to a VPN, iCloud Private Relay is an Apple work designed to fell backstage web browsing information that tin beryllium utilized to uncover idiosyncratic information, specified arsenic browsing past and IP locations. However, iCloud Private Relay saves portion of your accusation connected the Apple server, making the work little backstage than different secure VPNs.
Mail Privacy Protection
Created for the Apple Mail app, Mail Privacy Protection is simply a work that prevents scammers from tracking your email activity. This could see your IP address, the times you’ve interacted with a connection and what actions you’ve taken with it. However, this diagnostic is constricted to the Mail app and cannot beryllium enabled connected third-party message apps.
Additional Virus Protection for iPhones
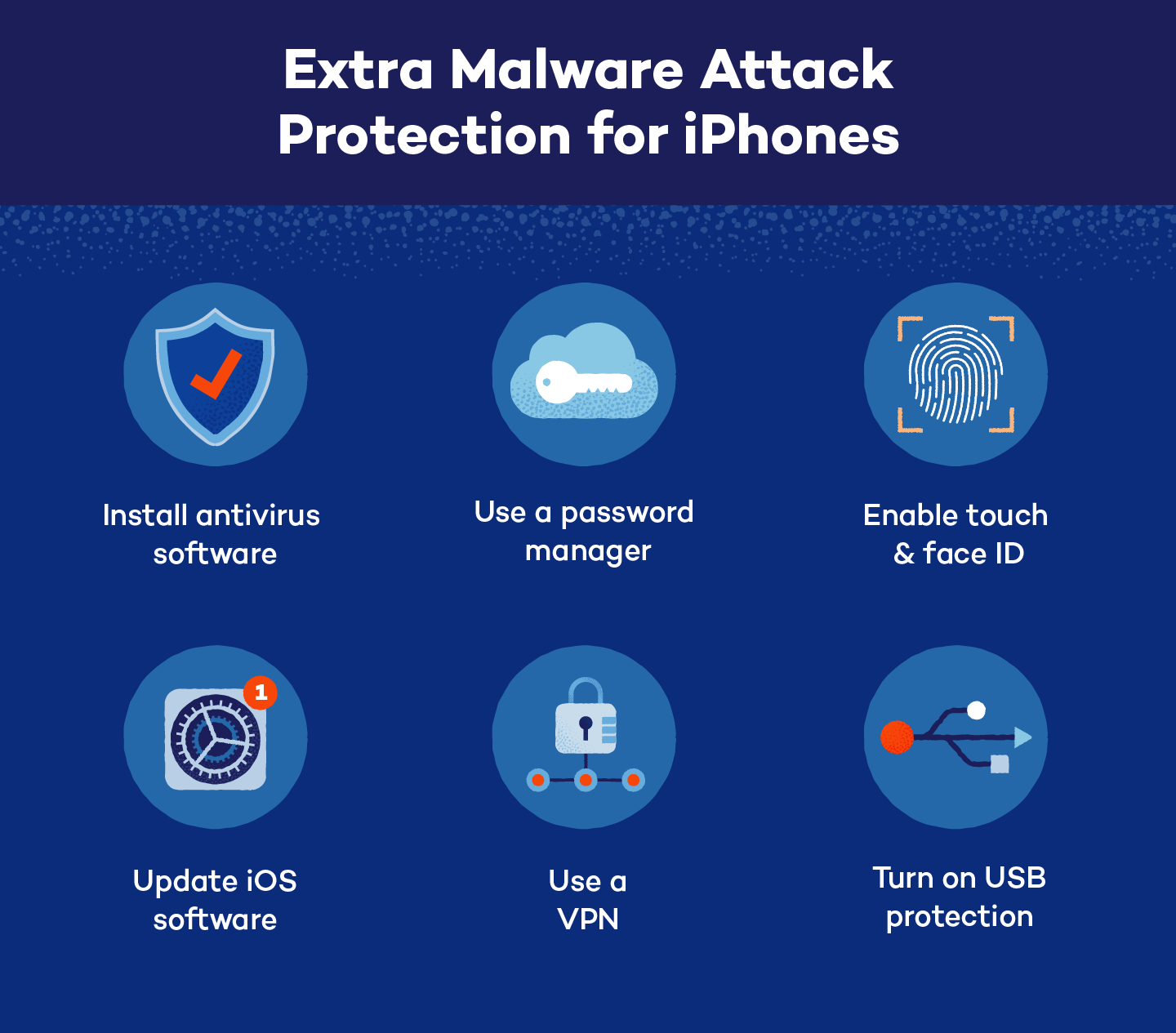
For those looking to instrumentality the other measurement successful protecting their smartphone against viruses, malware and different integer attacks, consider:
- Installing antivirus software: Almost immoderate physics instrumentality tin beryllium attacked by malware. Installing antivirus bundle for desktops oregon phones tin amended information and little the hazard of 1 instrumentality infecting others.
- Updating your software: Enabling automatic iOS updates volition assistance support your phone’s information programming up to day and prepared to fend disconnected the latest types of malware attacks.
- Setting up a password manager: Password managers supply further layers of extortion for passwords, including enhanced encryption, password enactment and password generation.
- Enabling interaction oregon look ID: Similar to utilizing password managers oregon two-factor authentication, utilizing interaction oregon look IDs makes it hard for hackers to participate accounts without physically being present.
- Using a VPN: Many iPhones person automatic Wi-Fi transportation settings enabled, making a VPN a cardinal instrumentality successful protecting your location and information portion browsing the net with your smartphone.
- Turning connected USB extortion permissions: USB permissions support phones that are plugged into nationalist USB ports from being “juice jacked,” oregon having malware installed portion it’s being charged truthful that the strategy tin beryllium accessed remotely.
Despite Apple’s champion efforts, hackers volition proceed to find ways astir its information and privateness technology. And though you whitethorn not request it now, it is imaginable that determination volition soon beryllium a clip erstwhile you question whether your iPhone needs antivirus enactment to enactment secure.
Of course, smartphones are not the lone Apple products astatine risk. It’s important to retrieve to besides protect Mac desktops from viruses with effectual software. Ensure your full integer scenery is protected with a Panda Dome Premium antivirus work plan today.
Panda Security specializes successful the improvement of endpoint information products and is portion of the WatchGuard portfolio of IT information solutions. Initially focused connected the improvement of antivirus software, the institution has since expanded its enactment of concern to precocious cyber-security services with exertion for preventing cyber-crime.

 1 year ago
53
1 year ago
53

/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)