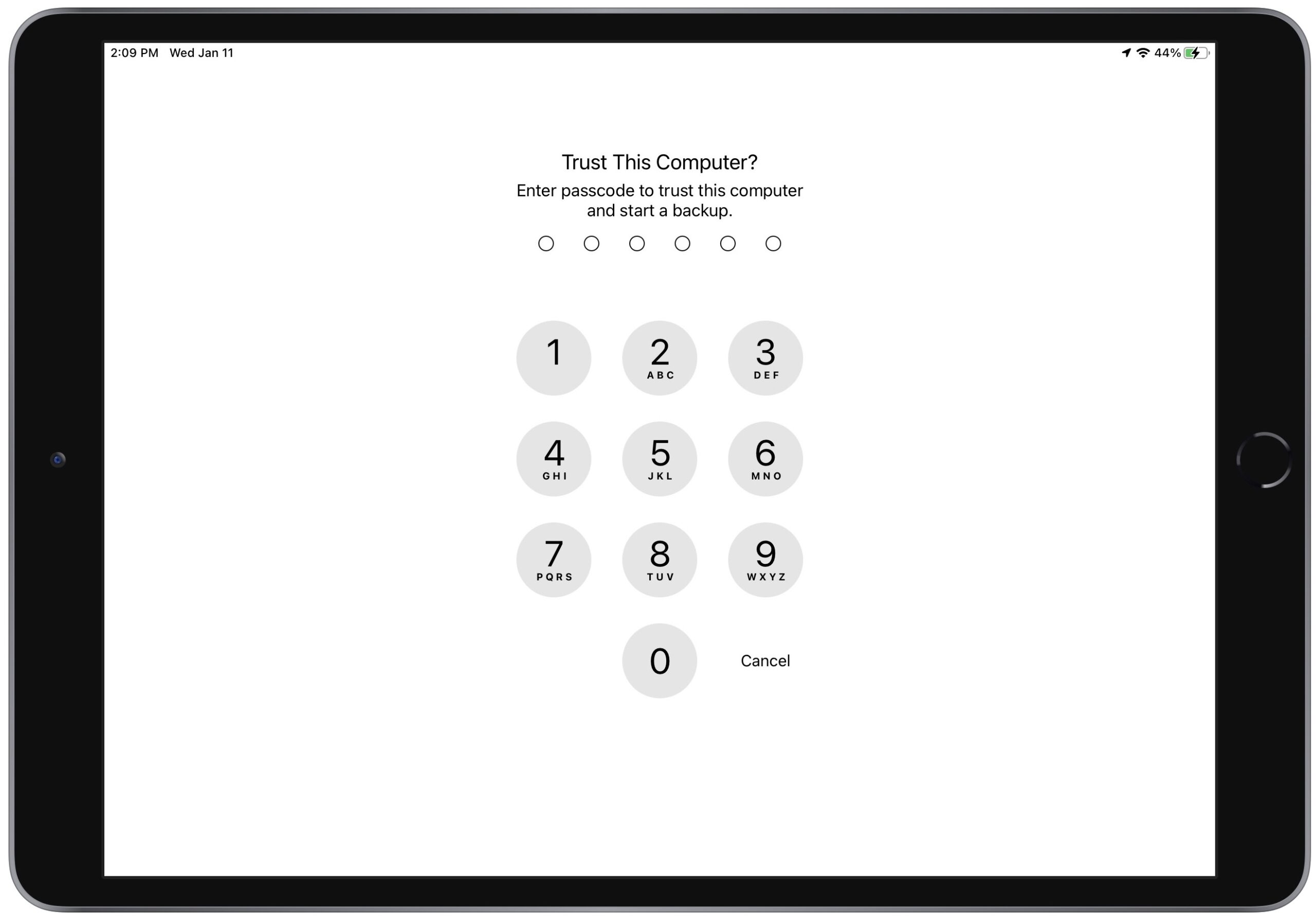
Back successful precocious October 2022, annoyed reports started to look connected TidBITS Talk complaining that connecting an iPhone oregon iPad to a Mac to backmost up oregon sync abruptly began to necessitate entering the device’s passcode each time. The “Trust This Computer?” passcode punctual appeared whether connecting via USB oregon Wi-Fi. It besides appeared erstwhile utilizing the iMazing inferior to trigger iOS instrumentality backups. Before this change, your instrumentality prompted for its passcode lone erstwhile it was freshly acceptable up and hadn’t yet connected to the Mac oregon erstwhile you connected to a caller Mac. (It’s besides imaginable you would get the punctual aft a large change, but that wasn’t documented oregon consistent.)
An iMazing blog post explains the situation. In iOS/iPadOS 16.1 and iOS/iPadOS 15.7.1, Apple started prompting connected each transportation successful effect to a vulnerability reported by information researcher Csaba Fitzl. In short, Fitzl showed that an attacker with carnal entree to your Mac and instrumentality could usage macOS’s AppleMobileBackup command-line inferior to trigger a backup to an unprotected location. Since section iOS/iPadOS backups deficiency encryption unless you adhd a password, the attacker mightiness beryllium capable to extract idiosyncratic information from the relocated backup.
It’s vanishingly improbable that this would ever happen: idiosyncratic would person to person entree to your unlocked Mac, your device, and the cognition to tally the exploit. It’s the benignant of vulnerability leveraged by authorities agents, criminals, and others with either state-authorized licence oregon nefarious intent.
Instead of preventing AppleMobileBackup from backing up to customized locations without further permission, Apple chose to mitigate the vulnerability by forcing the idiosyncratic to participate the device’s passcode connected each backup oregon sync connection. And it works: Apple’s caller attack prevents the backups from being directed to an unprotected determination unless an attacker knows your device’s passcode. If they cognize the passcode, there’s acold worse that they could bash with your iPhone oregon iPad and the information stored connected it.
Unfortunately, Apple’s solution is peculiarly ham-handed due to the fact that it adds a non-trivial measurement to every USB oregon Wi-Fi transportation effort by every iOS/iPadOS idiosyncratic who backs up oregon syncs locally. iCloud backups don’t endure from this requirement, but they necessitate an Internet connection, mightiness usage cellular data, and often request an iCloud+ subscription for the requisite retention space. Some radical besides don’t privation to spot Apple’s iCloud security, though the merchandise of Advanced Data Protection should trim that interest (see “Apple’s Advanced Data Protection Gives You More Keys to iCloud Data,” 8 December 2022).
More troubling is the mode that these nonstop passcode prompts volition desensitize users to entering their passcodes erstwhile asked. The much you’re asked for a password oregon passcode, the little attraction you pay, expanding the chances that you’ll autumn for a deceptive punctual from malware attempting to bargain your credentials.
Apple’s solution is besides overkill. As noted, the likelihood of an attacker with the skills to exploit this vulnerability having carnal entree to a user’s Mac and their iPhone oregon iPad is highly low. The solution is besides rather antithetic from Apple’s accustomed approaches to mitigating hazard from carnal attacks, which mostly connection ways to alteration oregon escalate the level of absorption depending connected your needs. A motivated attacker would beryllium much apt to fig retired however to encapsulate the exploit into malware that would past exfiltrate idiosyncratic information from the instrumentality backup, a invaluable vector that would astir apt beryllium sold to a authorities for a highly targeted attack. Yes, Apple’s information engineers should code the vulnerability, but they should bash truthful successful specified a mode that doesn’t interaction the wide idiosyncratic experience.
Practically speaking, you tin endure with entering the passcode connected each backup—it doesn’t forestall you from making backups but breaks automated backups with iMazing and whitethorn origin you to backmost up little often. For astir people, however, I urge iCloud backups due to the fact that they hap automatically, without immoderate quality interaction. Nor bash they devour abstraction connected your Mac, which tin beryllium significant, peculiarly if you person aggregate devices with tons of data.
Frankly, I was unimpressed with the wide idiosyncratic acquisition of the Mac-based instrumentality backup workflow arsenic well. While experimenting with section backups for this article, I had to propulsion the plug connected my iPhone 14 Pro backup earlier it zeroed retired the escaped abstraction connected my Mac. My iMac’s 1 TB SSD had astir 150 GB escaped aft backing up 32 GB from my 10.5-inch iPad Pro, and it was blessed to commencement backing up my iPhone 14 Pro, which has astir 112 GB used. Unfortunately, the backup wasn’t implicit erstwhile macOS warned maine that my disk was astir afloat with little than 3 GB available. The numbers should person worked retired but intelligibly didn’t, successful yet different illustration of wherefore escaped abstraction is hard for adjacent Apple to calculate.
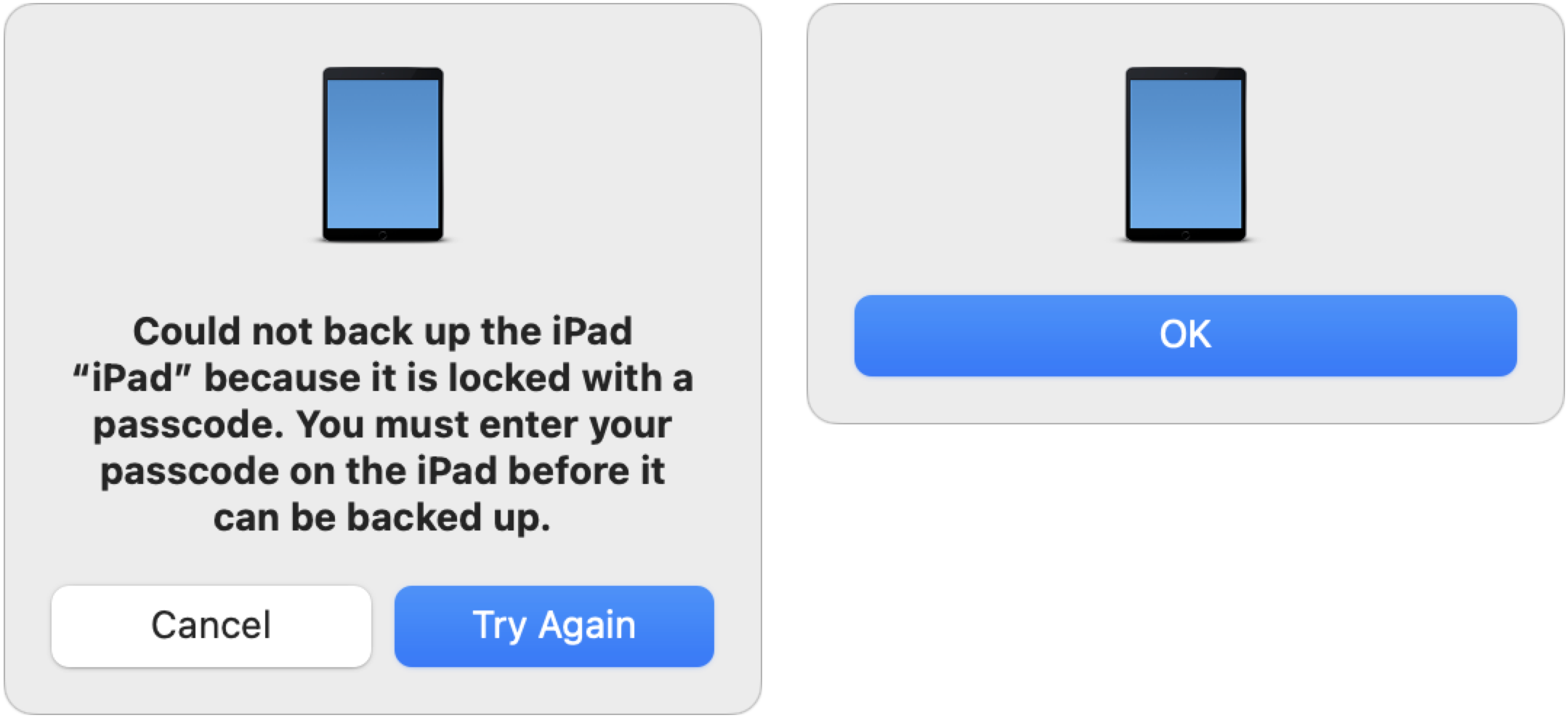
Plus, erstwhile I canceled 1 of the “Trust This Computer?” prompts connected my iPad, the Finder displayed the dialog connected the near below. Since I didn’t privation to effort again, I clicked Cancel and got the dialog connected the right. Talk astir amateur hour!
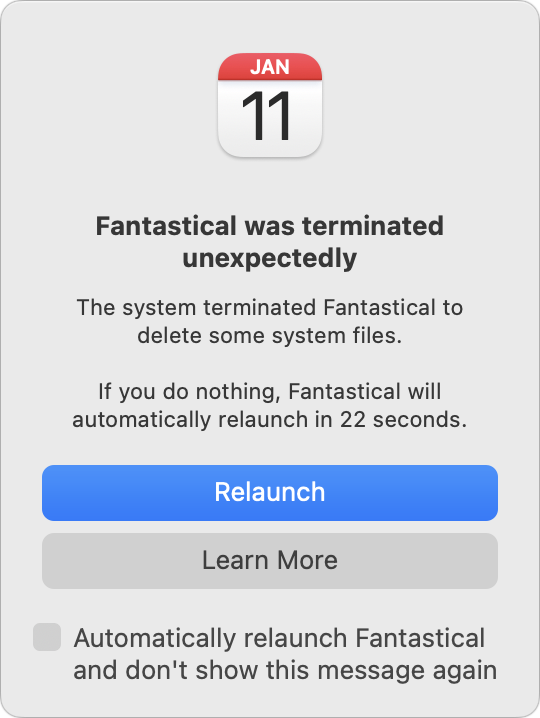
Finally, adjacent though macOS failed to cipher the magnitude of escaped abstraction correctly successful the end, it did recognize it would person to reclaim purgeable abstraction by deleting unnecessary files. That’s expected behavior, but it tin origin problems for apps, specified arsenic Fantastical, which alerted maine that it was unexpectedly terminated because of having its files deleted unexpectedly.
Apple’s alteration reinforces my penchant for iCloud backups, and I tin spot it causing galore radical to wantonness section backups and synchronization for iCloud. I’m not 1 to subscribe to conspiracy theories astir Apple utilizing information arsenic an excuse to propulsion radical into paying for iCloud+, but this poorly implemented solution doesn’t instill confidence. If Apple wants to dispel specified speculation, it should merchandise iOS and iPadOS updates that destruct the repetitious passcode request alongside versions of macOS that hole AppleMobileBackup properly.
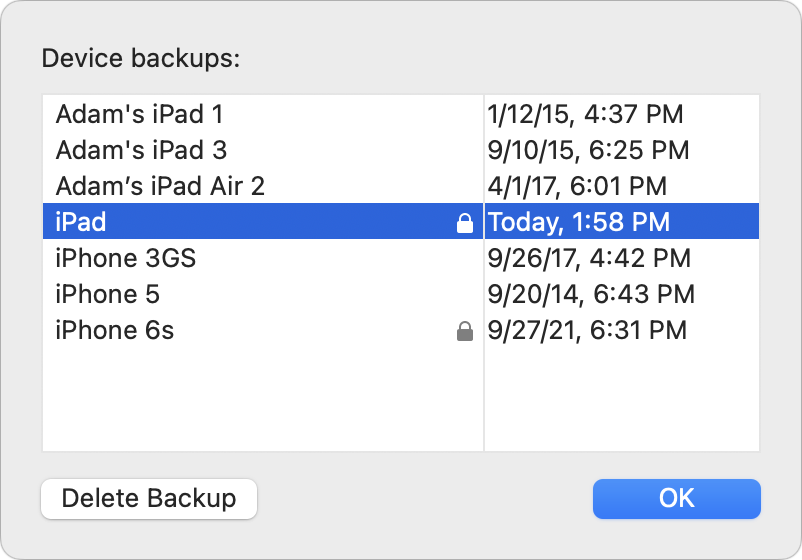
Now, if you’ll excuse me, I person to spell delete those section trial backups that conscionable ate each my escaped disk space. Luckily, Apple makes that easy. When managing an iOS instrumentality successful the Finder, click Manage Backups, prime the desired backup, and click Delete Backup. (You tin besides Control-click a backup and take Show In Finder to delete the backups manually.) Bye-bye, backups.

 1 year ago
64
1 year ago
64

/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)