Recently Sophos X-Ops investigated a caller bid of constricted attacks with malware that had unsocial characteristics that bespeak its creators and operators spent sizeable clip and effort to make covert methods of communicating with, and issuing commands to, the impacted devices.
While performing our investigation, we recovered that the menace actor(s) had installed astatine slightest 8 antithetic types of malicious files wrong of impacted devices.
As we saw successful a previous incident, these attackers created immoderate of these malicious files by modifying a fewer of the files that are utilized successful the SFOS operating system, portion others appeared to beryllium adjacent copies of “commodity” Linux malware, specified arsenic Gh0st RAT.
What follows is simply a defender’s investigation of the malware and its covert communications methods.
Hands successful the cookies JAR
These attacks began with exploitation of CVE-2022-3236 which is elaborate in Sophos Security Advisory sophos-sa-20220923-sfos-rce.
Parts of SFOS employment Java applications that tally nether the Jetty web server connected the device, itself. The menace actors modified a tiny fig of Java files that marque up parts of the device’s interior functionality, adding further codification into the files. This method preserves the device’s ain functions, truthful it remained operational contempt the modifications aft they overwrote the archetypal files with their modified versions.
Java JAR files typically incorporate 1 oregon much of what are known arsenic .class files; these .class files incorporate the functional programming of the Java application.
One of the files we discovered the attackers modified is simply a Java exertion named servlet-api-3.1.jar. The menace actors changed HttpServlet.class stored successful this JAR to adhd immoderate of their ain code, recompiled the JAR with the modified .class file, and uploaded the JAR into the affected devices.
This JAR checks the validity of HTTP methods that the server mightiness brushwood successful a web petition header (such arsenic a POST oregon a GET request). As such, it sits successful a captious presumption wherever it tin inspect characteristics of inbound web traffic.
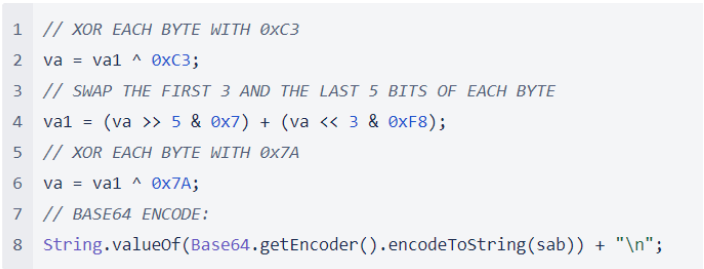 Figure 1: The encryption algorithm utilized by the modified httpservlet to encrypt stolen credentials
Figure 1: The encryption algorithm utilized by the modified httpservlet to encrypt stolen credentialsThe added codification gave the JAR record the quality to service arsenic a backdoor for the menace actors. It besides laic successful hold for a idiosyncratic oregon head to effort to log successful to the device, captured the logins and passwords successful existent time, past encrypted the stolen credential information utilizing a customized algorithm and wrote it retired to a record successful the /tmp/ directory connected the device.
The backdoor functionality was rather sophisticated. The menace actor(s) liable for this codification built a fewer safeguards into the process to guarantee that cipher but the menace actor(s) could usage the backdoor code. For instance, the codification added to this record parses the header contents of the inbound requests and checks for the beingness of a “JSESSIONID” cardinal successful the Cookies header.
Content nether this header worth gets processed by the caller code, which decrypts the contents of this JSESSIONID worth utilizing a method that uses the numeric values for the period and the time of the period to cipher the key, which means that the cardinal utilized to decrypt the information changes each day, but is predictable by the algorithm.
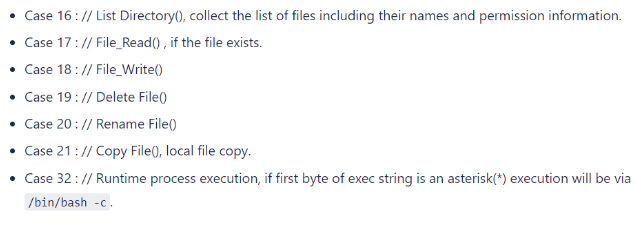
The decrypted archetypal byte of the web requests information watercourse contains a abbreviated worth that points to 1 of 7 antithetic types of commands they tin execute. In brief, the Trojanized codification tin database directories; read, constitute to, copy, delete, oregon rename idiosyncratic files; oregon execute commands successful the autochthonal ammunition connected the device.
Figure 2 The bid “cases” utilized by the modified httpservlet
There’s thing antithetic astir this benignant of data; JSESSIONID is simply a normal, morganatic benignant of accusation that tin beryllium passed via a cooky to a Java servlet. The usage of this method to instruct the malware to bash this is incredibly subtle and precise covert, and highly antithetic successful much accepted malware.
The attackers person feedback telemetry from the trojanized record astir some palmy and unsuccessful attempts to usage the trojan codification functions.
Attackers driblet a atrocious ELF ammunition stager
During the exploit process, the attackers Trojanized morganatic files usually contiguous connected the instrumentality (named screenmgr.pl and WebsocketServer.pm). The attackers modified the screenmgr file specified that, erstwhile the attackers killed and restarted the process, it had (and could keep) ‘root’ level permissions. This record past sets up WebsocketListener, which past works with the trojanized mentation of WebsocketServer to supply Perl-based eval as a basal user. Along with these modifications, we besides saw it present a tiny ELF executable, successful the signifier of a tiny blob of base64-encoded data.
The wide intent of this ELF binary (Linux/Loit-X) is to acceptable the equine namespace of the process to the aforesaid arsenic /proc/1/ns/mnt and telephone a shell. This binary provides a equine namespace breakout arsenic agelong arsenic the autochthonal procfs is not isolated from the discourse of the exploited process and arsenic agelong arsenic the process hasn’t been hardened by seccomp to restrict strategy calls to “setns”. Given services are leveraging seccomp to forestall calls to “setns”, amongst different hardening measures, and the exploit codification does not look to telephone this record it would look this is simply a remnant from erstwhile the attackers were processing and investigating their exploit and they whitethorn person been unsuccessfully targeting services straight astatine an aboriginal signifier earlier pivoting their people to different process structure.
Custom Metasploit module
During the attacks connected immoderate devices, the menace actor(s) delivered a customized JAR Metasploit module based connected an existing payload named Payload.java. On affected systems, we recovered that this record was written to the device’s record retention arsenic a record named syslog-ng.cfg.
The Metasploit module was arsenic adjacent to “stock” from the company’s Github arsenic possible, with the lone changes being the configuration information utilized by the Metasploit module to specify its command-and-control server address, and the larboard fig it volition link to.
We were capable to find that, erstwhile this record was running, it would make a transcript of itself named /tmp/~spawn[randomChars].tmp.dir. After each execution, the record tries to delete itself.
Malicious backdoor functionality successful SessionAgent
We recovered astatine slightest six antithetic variants of an ELF binary malware we notation to as Linux/Backdr-NQ. The malware named its main class CResoule and contained a configuration record encrypted utilizing the RC4 algorithm.
It establishes persistence by appending its execution way to a record named /etc/rc.d/S00null that executes astatine bootup.
The malware contained respective command-and-control addresses. The bot appears to usage a time-based effect that randomizes a caller AES cardinal for each progressive transportation session. The malware archetypal sends this cardinal to the C2 server past uses the cardinal to encrypt outbound connection with the C2 portion the transportation is active. Its embedded config includes a way for an outer AES-encrypted config record to beryllium loaded arsenic an override of its embedded config, specified as /var/cache/update.log.
The malware has a diagnostic that checks inbound postulation for a circumstantial byte and executes assorted types of backdoor functions based connected that value. The bot tin beryllium instructed to upload files to the C2 (or download record from there), modify its ain configuration, execute a bid connected the device, oregon adjacent the transportation to the C2.
Termite malware delivered via Clientless VPN
Digging further into the impacted devices, we recovered information connected immoderate devices that pointed to yet different distant entree trojan successful use. The malware (which we present observe arsenic Linux/Gognt-O) is simply a UPX-packed ELF binary, astir 2.3MB successful size. During its connection, the malware writes retired a log enactment that includes the drawstring “Termite (v [number]) starting…” with a very, very specific mentation fig of 2.0200204206304400404
The malware is simply a emblematic backdoor with the added functionality of being capable to service arsenic a SOCKS proxy, which would let it to intercept the contents of immoderate kinds of web traffic.
Another Gh0st RAT strikes
Some machines were the recipients of 1 of astatine slightest 3 variations connected the Gh0st RAT ELF binary (detected arsenic Linux/Rekoobe-A). As successful the CVE-2022-1040 attack, the attackers built a malware that inspects each ping packets, waiting for a specially crafted ping packet that would not, otherwise, hap “in nature.”
The ping packet, if validated correctly, tin beryllium utilized to trigger the instrumentality into either opening a reverse ammunition backmost to the code provided by the attacker (that code being delivered wrong the ping packet’s “data” section), oregon it volition hindrance and perceive connected port 31234 to judge a transportation from a C2. The bot makes an further validation cheque erstwhile a transportation is established. This method is known arsenic Traffic Signalling, and is elaborate arsenic method T1205 successful the MITRE ATT&CK framework.
Conclusion
As we see, these targeted attacks mixed some customized and commodity malware seeking to make screen channels to power the devices. In addition, the attackers took steps to fell their tracks. Combined, these actions created a hard-to-detect onslaught the demonstrates a blase menace histrion seeking to maximize their power of the instrumentality portion minimizing the risks of detection.
Indicators of Compromise (IoCs)
We are making IoCs available on our GitHub here.


/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)