
Hackers person been exploiting a now-patched vulnerability successful VMware Workspace ONE Access successful campaigns to instal assorted ransomware and cryptocurrency miners, a researcher astatine information steadfast Fortinet said connected Thursday.
CVE-2022-22954 is simply a distant codification execution vulnerability successful VMware Workspace ONE Access that carries a severity standing of 9.8 retired of a imaginable 10. VMware disclosed and patched the vulnerability connected April 6. Within 48 hours, hackers reverse-engineered the update and developed a moving exploit that they past utilized to compromise servers that had yet to instal the fix. VMware Workspace ONE entree helps administrators configure a suite of apps employees request successful their enactment environments.
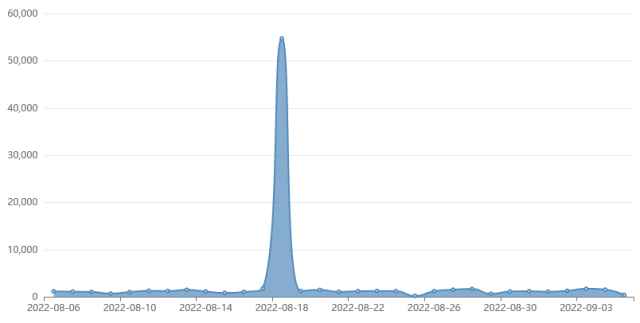
In August, researchers astatine Fortiguard Labs saw a abrupt spike successful exploit attempts and a large displacement successful tactics. Whereas earlier the hackers installed payloads that harvested passwords and collected different data, the caller surge brought thing else—specifically, ransomware known arsenic RAR1ransom, a cryptocurrency miner known arsenic GuardMiner, and Mirai, bundle that corrals Linux devices into a monolithic botnet for usage successful distributed denial-of-service attacks.
FortiGuard
“Although the captious vulnerability CVE-2022-22954 is already patched successful April, determination are inactive aggregate malware campaigns trying to exploit it,” Fortiguard Labs researcher Cara Lin wrote. Attackers, she added, were utilizing it to inject a payload and execute distant codification execution connected servers moving the product.
The Mirai illustration Lin saw getting installed was downloaded from http[:]//107[.]189[.]8[.]21/pedalcheta/cutie[.]x86_64 and relied connected a bid and power server astatine “cnc[.]goodpackets[.]cc. Besides delivering junk postulation utilized successful DDoSes, the illustration besides attempted to infect different devices by guessing the administrative password they used. After decoding strings successful the code, Lin recovered the pursuing database of credentials the malware used:
|
hikvision |
1234 |
win1dows |
S2fGqNFs |
|
root |
tsgoingon |
newsheen |
12345 |
|
default |
solokey |
neworange88888888 |
guest |
|
bin |
user |
neworang |
system |
|
059AnkJ |
telnetadmin |
tlJwpbo6 |
iwkb |
|
141388 |
123456 |
20150602 |
00000000 |
|
adaptec |
20080826 |
vstarcam2015 |
v2mprt |
|
Administrator |
1001chin |
vhd1206 |
support |
|
NULL |
xc3511 |
QwestM0dem |
7ujMko0admin |
|
bbsd-client |
vizxv |
fidel123 |
dvr2580222 |
|
par0t |
hg2x0 |
samsung |
t0talc0ntr0l4! |
|
cablecom |
hunt5759 |
epicrouter |
zlxx |
|
pointofsale |
nflection |
admin@mimifi |
xmhdipc |
|
icatch99 |
password |
daemon |
netopia |
|
3com |
DOCSIS_APP |
hagpolm1 |
klv123 |
|
OxhlwSG8 |
In what appears to beryllium a abstracted campaign, attackers besides exploited CVE-2022-22954 to download a payload from 67[.]205[.]145[.]142. The payload included 7 files:
- phpupdate.exe: Xmrig Monero mining software
- config.json: Configuration record for mining pools
- networkmanager.exe: Executable utilized to scan and dispersed infection
- phpguard.exe: Executable utilized for guardian Xmrig miner to support running
- init.ps1: Script record itself to prolong persistence via creating scheduled task
- clean.bat: Script record to region different cryptominers connected the compromised host
- encrypt.exe: RAR1 ransomware
In the lawsuit RAR1ransom has ne'er been installed before, the payload would archetypal tally the encrypt.exe executable file. The record drops the morganatic WinRAR information compression executable successful a impermanent Windows folder. The ransomware past uses WinRAR to compress idiosyncratic information into password-protected files.
The payload would past commencement the GuardMiner attack. GuardMiner is simply a cross-platform mining Trojan for the Monero currency. It has been progressive since 2020.
The attacks underscore the value of installing information updates successful a timely manner. Anyone who has yet to instal VMware’s April 6 spot should bash truthful astatine once.


/cdn.vox-cdn.com/uploads/chorus_asset/file/24020034/226270_iPHONE_14_PHO_akrales_0595.jpg)






 English (US)
English (US)